Increase in phishing emails
Recently we’ve become aware of an increase in phishing emails, especially relating to Microsoft Office 365 and cPanel password change requests. Learning how to spot phishing emails is an important skill for anyone who uses email, whether at work or at home. We therefore thought it was an appropriate time to compile some useful tips on how you can recognise phishing emails, so you are not tempted to respond and disclose any personal information.

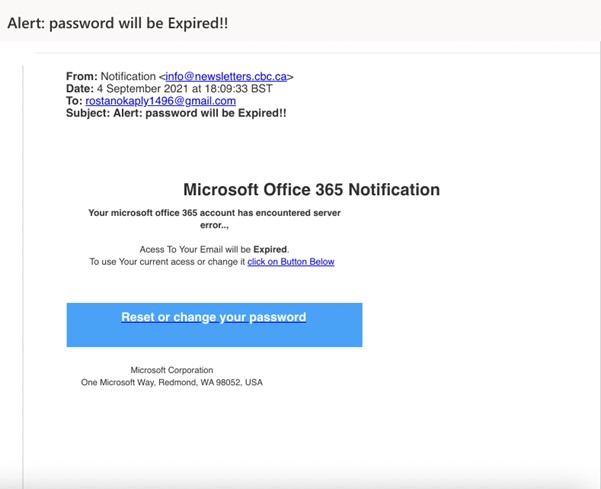
What are phishing emails?
Phishing emails are fake emails with the intent of deceiving the receiver into providing confidential information such as passwords, credit card numbers, addresses, date of birth, social security numbers and so forth.
An example of a common phishing email is illustrated here. In this case it is targeted at Office 365 users with the intent of tricking the user into disclosing their email password.
Phishing email checklist
Remember to check for the following signs
1. Check the domain name/sender’s email address
Legitimate companies use their own company domain email addresses to send communication; not public domain names like gmail.com or hotmail.com or yahoo.com. If the email address is from a private domain name, do a quick google search to verify the company before you do anything else. In the example above, cbc.ca doesn’t appear to be a commonly used domain and appears suspicious. Check the email address and not just the display name to make sure the sender is not spoofing a known contact. Check the message headers to clarify that the email address in the header matches the email address the message has apparently come from – these should match. The method to do this varies by mail provider, but in Outlook, open a message and select File > Properties > Internet Headers.
2. Check the grammar
Often phishing emails are poorly written and have spelling mistakes. If the English seems inconsistent and the grammar is poor, even though the email appears to be from an official source such as the government or a large corporation, then beware it might be fraudulent. In the example above, the phrase “To use Your current access or change it” has several grammatical errors, random capitalisation, lack of punctuation and coherency which suggests the email is fake.
3. Nature of the email
Peruse the content of the email and gauge what it is about. If it is an email specifically asking you for sensitive information, such as verifying your credit card details, or your home address, passport no etc then do not respond. Legitimate companies are very unlikely to ask you for sensitive information by email. Another tactic is to create a sense of urgency to rush the recipient into disclosing personal data. For example, this might be about unpaid invoices or the imminent suspension of services. Another popular phishing email is to tell the receiver they have won a prize or a monetary reward that prompts them to click on links/fill in forms. In this email in particular, the sender is requesting password information so they can access personal details.
4. Watch for unsolicited attachments/URL links
Hackers often send pictures or downloads that have viruses that can infiltrate your software. Ensure you do not click on any of these and instead if you do want to open a URL link to your bank or social media, open a separate window and sign in.
5. Filter your emails and delete
Most emails that are not from legitimate senders automatically get filtered into junk. However, sometimes the odd fake email will be delivered. Make sure to go to settings and choose the relevant criteria – automatic, low, high or safe lists only. For example: by clicking safe lists option in your junk email drop down menu in Outlook, you can ensure the emails you receive are from your contacts only.
For further reading, Microsoft have published a list of anti-phishing tips specifically for Microsoft 365 and Outlook to further expand your skills in spotting phishing emails. Our IT support team can also provide training and active assistance in maintaining safe and secure email correspondence, so please do contact us today for further information about email security and support.
